StealthWAN
Make your network InvisibleStealthWAN
StealthWAN
StealthWAN makes your systems invisible to the rest of the world allowing you to securely expand your operations to the extreme network edge.
✓ STEALTH Network Perimeter
✓ World Class Encryption
✓ Remote Certificate Management
✓ Seamless Network Failover
✓ Zero Hands Deployment
✓ STEALTH Network Perimeter
✓ World Class Encryption
✓ Remote Certificate Management
✓ Seamless Network Failover
✓ Zero Hands Deployment
Solution Architecture
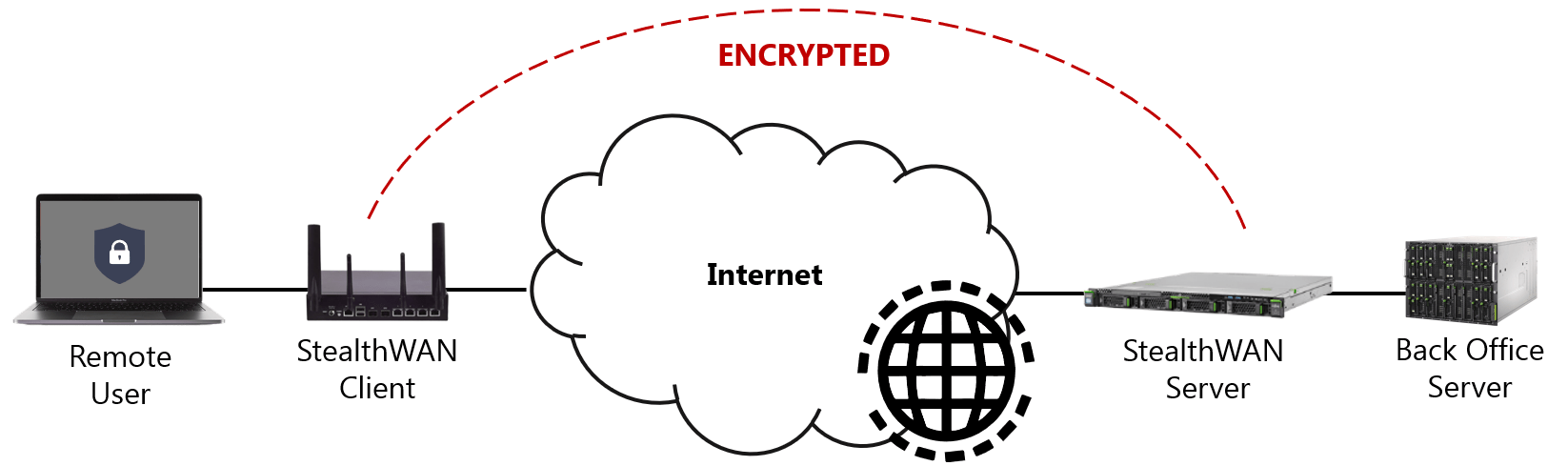
Wide Area Network Encryption
Mitigating risks associated with network infrastructure and service providers, the StealthWAN solution encrypts network data whilst making endpoints impervious to external attacks. Combined with the unique hands-off-install, the solution is a rapidly deployable, highly secure WAN Encryption solution.
Greatly increase the security of your network perimeter using StealthWAN to obfuscate your Wide Area Network (WAN) from external threats whilst encrypting all communications between Head Office, Branches and Internet of Things (IoT) devices.
Features
- Secure communications platform
- AES 256, TLS 1.2, SHA512 Encrypted links
- Integrates into existing Certificate Authorities
- Resilient connectivity through multiple MNOs
- Central configuration & policy management
- Automated deployment systems
- Patented STEALTH security offering
- Can be customised based on requirements
- Supports dynamic routing protocols
- Software and Hardware solutions
- Stateful firewall
StealthWAN
Why StealthWAN
Stealth
Choose between Version 1 and Version 2 of the patented STEALTH security offering.
Encryption
Military grade encryption with TLS 1.2 encapculation to protect information at a “Top Secret” level.
Compliance
Designed for PCI DSS v3.2 and NIST compliance.
Service Reliability
Integrates into all major technology vendors, monitoring solutions and certificate authorities.
Reduced Networking Costs
Leveraging the internet as a transport layer, a company can mitigate the requirement for expensive MPLS and APN network contracts.
Deployment
Rapid/Automated deployment model to ensure your new stealth network is seamlessly integrated with your current network infrastructure.
Cost
Lower Total Cost of Ownership than other secure crypto communications solutions.
Skills and Customizations
No requirement for rare or expensive skills in administration or when requiring customization based on your specific requirements.
Critical Infrastructure Use Case
Cyber-attacks on critical infrastructure can have catastrophic consequences on essential systems, including disrupting energy, transportation, and healthcare, leading to widespread chaos, economic losses, and even threats to public safety.
Protecting critical infrastructure is paramount in today’s digital landscape.
Pfortner’s StealthWAN solution offers a robust defence mechanism against cyber threats, safeguarding essential infrastructure from potential breaches and disruptions. StealthWAN ensures secure and reliable communication networks for critical systems by encrypting data transmissions and implementing dynamic connectivity selection while making your network invisible to the outside world.
Engage
