Thoughts Insights & Opinions
When AI fails…
....Artificial Intelligence (AI) is like that quirky friend who sometimes gets things hilariously wrong. Case in point, Google's recent search AI blunder, identifying Obama as a Muslim. Ps, this is definitely not the case … ( see the CNN article about Obama HERE)...
Another Day, Another Data Leak
Last week it was reported that, Dell, a prominent technology company, experienced a significant breach that compromised its systems. What Happened? Hackers managed to gain unauthorized access to Dell's servers, enabling them to extract sensitive data from the...
Cyber Risk is VUCA!
VUCA means environments or systems that are Volatile, Uncertain, Complex and Ambiguous From an alarming report by SABRIC, it is clear that cyber risk and crime is on the rise. The recent CIPC hack, as a stark reminder of the potential risks and vulnerabilities...
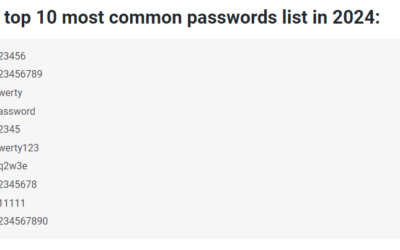
It’s time to break up with Password@123
In 2024, our password habits seem to be stuck in a nostalgic loop, with "123456" still reigning as the champion of predictability. This illustrious list of the top 10 most common passwords includes all-time hits like "password" and "qwerty," not to mention their...
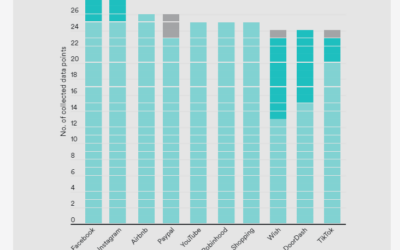
Which Apps track you (the most)
The erosion of user privacy continues… In our digital age, privacy comes at a cost, and it's plummeting. One would expect a mobile app to track some usage data to enhance the product but the recent banning of TikTok situation has shed new light on data collection....
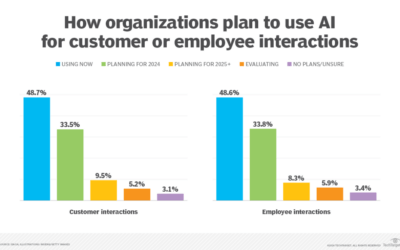
Does AI increase communications risks?
As depicted above, a global study by Metrigy found that nearly half of the contacted companies are leveraging AI for customer engagement and internal collaboration. This is great for productivity and efficiency but has raised significant security concerns, including...
CEOs vs Cybersecurity Incidents
Cyber Incident: what’s a CEO to do? According to the UK National Cyber Security Centre - cybersecurity has become a paramount concern for organisations of all sizes. As leaders, every CEO plays a crucial role in both preventing and responding to cyber incidents; below...
How nonverbal communication can determine your future
71 million people have watched a TED talk by Amy Cuddy; it is one of the most-watched talks ever. She speaks on how body language can influence ourselves and others and how it can positively impact our life achievements. Why would 71 Million watch this? Many people...
Dodged a bullet here…
The recent revelation about the xz Utils backdoor attempt has sent shockwaves through the open-source community, highlighting a significant risk in the software supply chain. The non-technical version:In simple terms, a critical tool used by almost all Linux systems,...