Thoughts Insights & Opinions
Olympics a Prime Target
The 2024 Paris Olympics has faced multiple security threats. It comes as no surprise that great event also creates a platform for some nefarious parties… What was predicted? Chris Clough predicted these Top 5 Risks HERE. Terrorism Cybersecurity Crime and Public Safety...
CrowdStrike explained to a normal person
Who is CrowdStrike? CrowdStrike (website HERE) is a leading cybersecurity company providing Cyberdefence. Their solutions include endpoint protection, threat intelligence, and incident response services. What caused the global outage? According to Reuters...
Nullbulge Hack Disney’s Slack
Disney's Slack channels were hacked, exposing sensitive company information. According to CNN, the hacker group "Nullbulge" leaked internal conversations and details about future projects. Why Disney? The group claimed artist contracts, and its approach to AI as...
Largest Password Leak Ever
RockYou2024 A new data breach named "RockYou2024" has surfaced. According to the Cybernews article HERE, it contains more than 8.4 billion passwords. This leak may be the largest in history; some other huge breaches are recorded HERE. The data was posted on a...
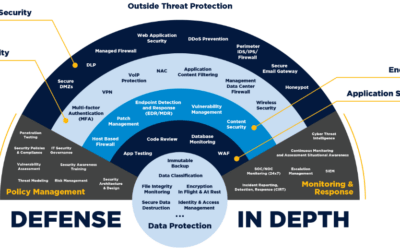
Cyberattack – Survivor Account
A Survivor’s Tale TeamViewer recently rebuffed a Cyber Attack using Defence in Depth (DID) as shared HERE DID can be defined as protecting your house with a fence, a locked door, a security alarm and a really big Boerboel. The recent TeamViewer attack by hacker group...
Digital Self Defence
"Cybercrime Self-Defence" by Craig Rosewarne This is a brilliantly practical guide to staying safe online and is available HERE Craig explains the cyber threat landscape, highlighting the rapid growth of cybercrime. Insights "Cybercrime Self-Defence" discusses...
Ethical Artificial Intelligence
A Call for Accountability. Edward Snowden recently criticized OpenAI (HERE), accusing them of betraying public trust. He argues that OpenAI's practices contradict their mission of benefiting humanity. PS. Elon Musk made similar accusations HERE. The Concern....
Avoiding Cybersecurity Slip-Ups
The Five Most Common Mistakes Ever left your front door wide open?In the digital world, many are doing just that without realizing it!Visual Capitalist’s article highlights five common cybersecurity blunders HERE First up, there's the classic "Password123" saga.Using...
Banks are the Targets
Cybercriminals are targeting banks. According to World Economic Forum (HERE), Global financial stability at risk due to cyber threats. In cybersecurity terms, banks are facing immense challenges. This is highlighted by a recent data breach involving Santander...