The Downward Path to Price
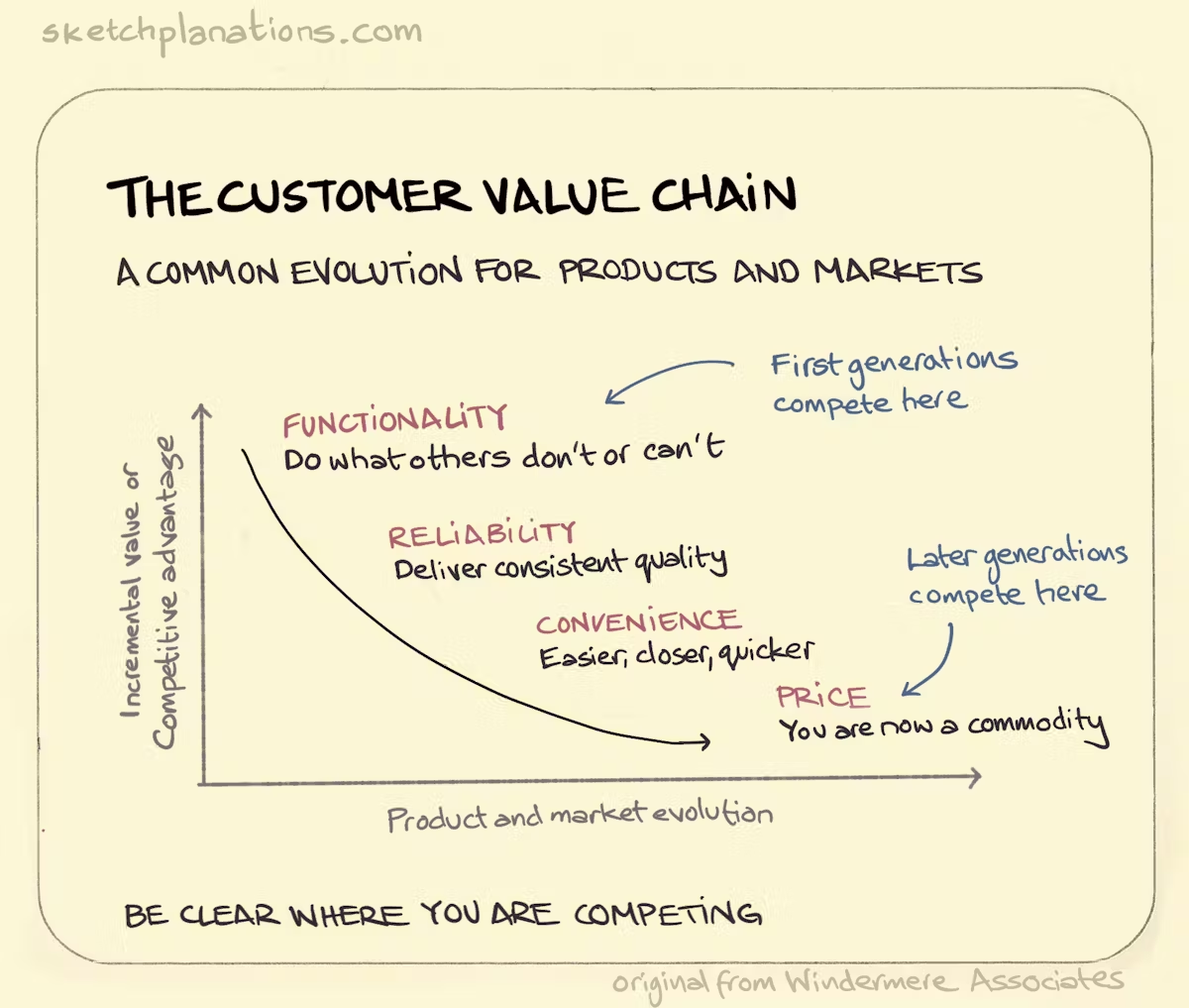
Cybersecurity solutions evolve just like any other product. The Customer Value Chain highlights this journey from differentiation through functionality to eventual commoditization.
Early cybersecurity innovations thrive on functionality, offering unique capabilities like zero-trust architectures or advanced threat intelligence.
As competition increases, reliability becomes key, ensuring solutions provide consistent protection with minimal false positives.
Next, convenience drives adoption, with businesses prioritizing seamless integrations, automation, and user-friendly security platforms.
Eventually, security solutions risk becoming commodities, competing mainly on price, reducing differentiation.
For cybersecurity firms, the key is to know where you compete.
Innovators must push the boundaries of functionality, while established providers should focus on reliability and usability to retain a competitive edge.
Companies that fail to differentiate risk being undercut by cheaper, less effective alternatives.
In cybersecurity, staying ahead means continuously moving up the value chain, before your service becomes just another commodity.
________
One more thing, at Pfortner, we take communications privacy very seriously. We encrypt email, messaging and network communications to provide our clientele with uncompromised privacy.
If you need to protect sensitive communications, please see www.pfortner.co.za or send an email to info@pfortner.co.za, and we will get back to you.